Multi-level marketing systems run on replicated sites, mobile apps, and countless distributor devices. So, one tiny misstep (a sloppy script, an open bucket, a weak login) can echo across your whole network.
You’re also holding sensitive gold: PII, KYC files, commission ledgers, and payout details, exactly what attackers hunt for.
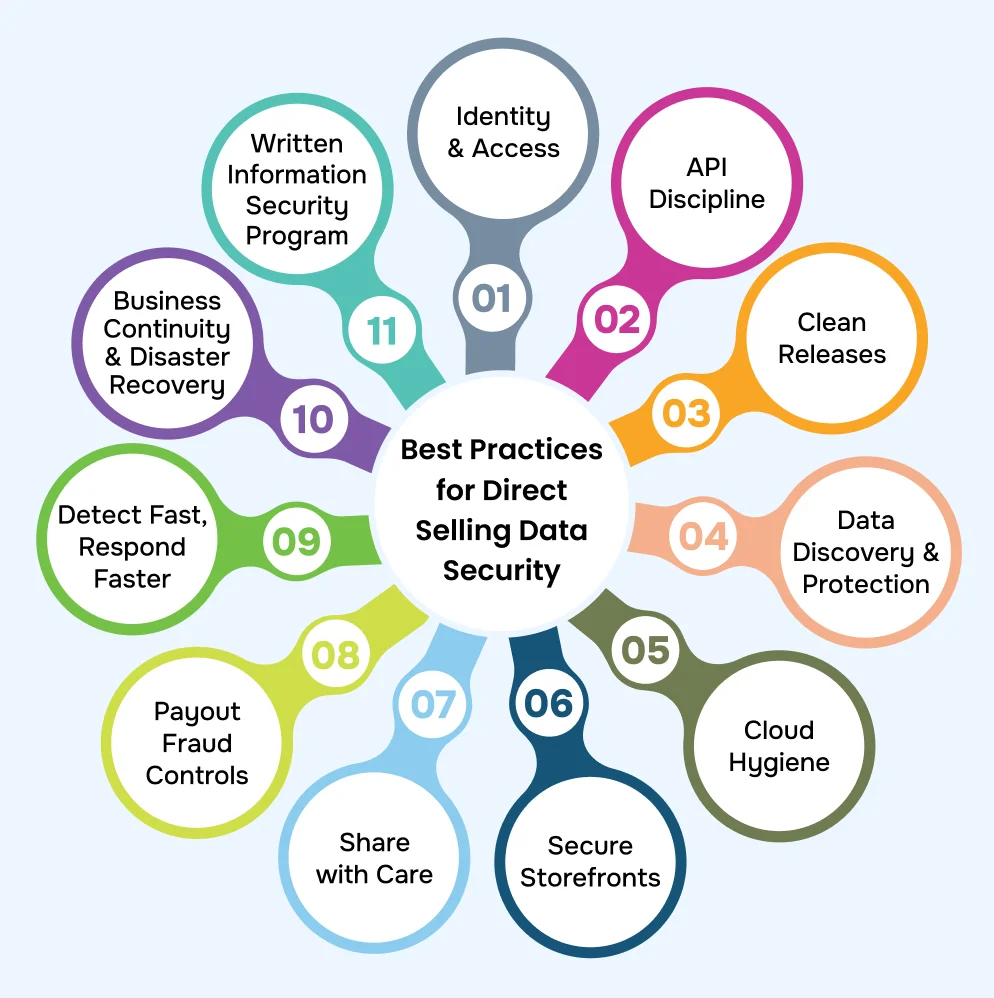
This above-added infographic turns “security” into a practical Minimum Viable Security (MVS) routine you can run every release: confirm real identity before access, filter traffic at the API edge, ship code that’s been scanned and signed, discover and encrypt sensitive data, harden cloud and storefronts, control sharing and payouts, detect anomalies fast, and rehearse your recovery. Start simple, measure what matters, and keep tightening the loop.
Identity & Access: Run every API through a gateway with authentication, rate limits, IP rules, and per-request logging. Block bad traffic at the edge before it ever touches your core application. Consistent request/response auditing makes investigations fast.
API Discipline: Run every API through a gateway with authentication, rate limits, IP rules, and per-request logging. Block bad traffic at the edge before it ever touches your core application. Consistent request/response auditing makes investigations fast.
Clean Releases: Bake security into Continuous Integration and Continuous Delivery (CI/CD): run Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Software Composition Analysis (SCA) on each build and fail the pipeline on critical findings. Cryptographically sign images/bundles to prevent tampering in transit, and track approvals and change notes for every production release.
Data Discovery & Protection: Auto-find PII, KYC documents, and payout/banking details across databases and storage. Tag them as sensitive, encrypt at rest (e.g., AES-256) and in transit, and show masked/tokenized values to most users. Grant real data access strictly on a need-to-know basis.
Cloud Hygiene: Catch misconfigurations early (e.g., publicly accessible storage buckets, open network ports) and block them before deployment. Use private endpoints, such as AWS or Microsoft Azure Private Link, within your Virtual Private Cloud (VPC) or Virtual Network (VNet) instead of exposing services to the public internet. Separate production and staging environments, and apply the Principle of Least Privilege (PoLP) to both human users and service identities.
Secure Storefronts: Enforce a tight Content-Security-Policy (CSP) to control where scripts/styles can load from. Turn on HSTS so browsers always use HTTPS and can’t be downgraded. Where possible, use subresource integrity for third-party scripts.
Share with Care: Tie every export to a named user, timestamp it, and give the link a short expiry. Export only the columns needed, i.e., no “everything” dumps. Trigger alerts and require manager approval for bulk or repeated exports.
Payout Fraud Controls: Match payouts to verified identities and flag odd patterns (new bank details + large payout + new device, etc.). Any change to payout info requires MFA plus higher-role approval. Keep auditable trails of who changed what and when.
Detect Fast, Respond Faster: Centralize logs in a Security Information and Event Management (SIEM) platform so signals correlate across applications, APIs, and cloud services. Add User and Entity Behavior Analytics (UEBA) to learn normal behavior and flag anomalies early. Enable one-click isolation of risky devices, and rehearse incident-response runbooks until the steps feel like second nature.
Business Continuity & Disaster Recovery: Maintain a Business Continuity and Disaster Recovery (BC/DR) plan with clearly assigned owners, explicit Recovery Time Objective (RTO) and Recovery Point Objective (RPO) targets, and scenario playbooks. Pre-draft notification templates for regulators and for customers/distributors. Run restore drills regularly until you consistently meet your RTO/RPO targets.
Written Information Security Program: Your Written Information Security Program explains what to protect, how you protect it, who is accountable, and how you will prove it. Include scope, RACI, policies, standards, and step-by-step procedures. Update it when tech, vendors, or regulations change.

