MLM Security Management
Secure Every Layer of Your Business Operations With Global MLM's Security Management System
Protect your MLM business at every level. Get real-time alerts, identity checks, and fraud detection that works around the clock.

Real-Time Fraud Detection

Encrypted Data & Access Control

Secure User Identity Verification

FTC & DSA Compliance Support
What is MLM Security Management in Multi-level Marketing Software?
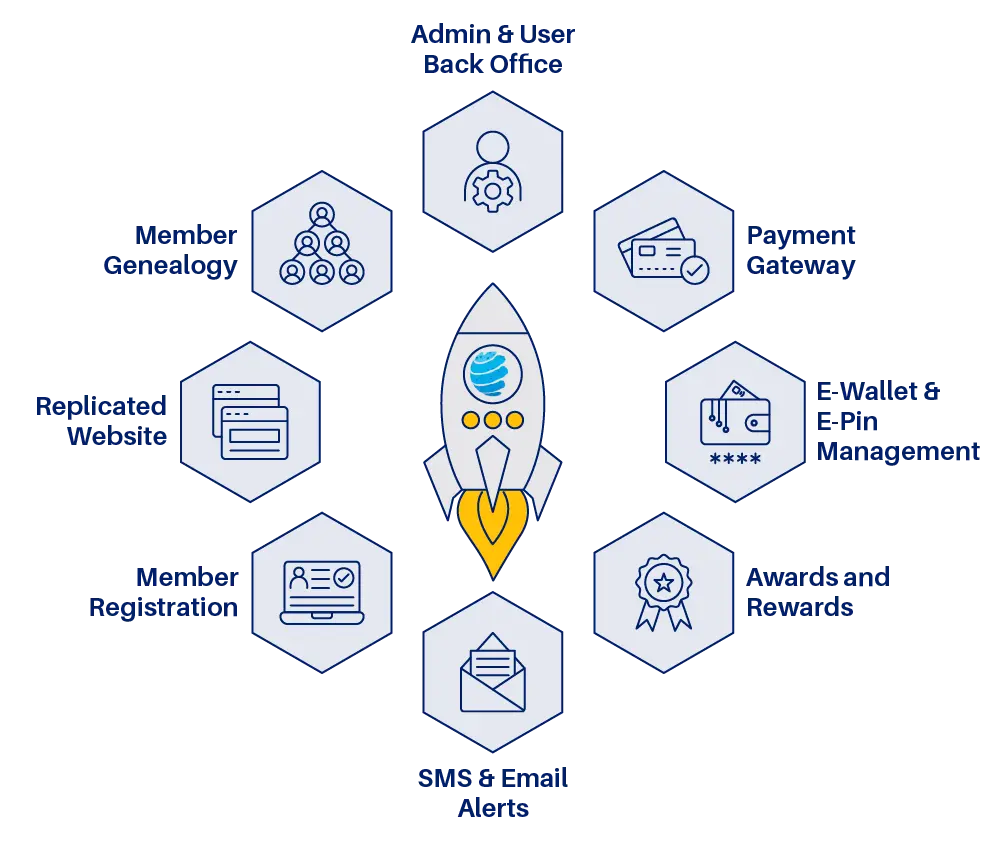
What is MLM Security Management in Multi-level Marketing Software?

An MLM Security Management System is an in-built software module designed to protect a multi-level marketing (MLM) business from fraud, data leaks, misuse, and compliance issues. It makes sure every action in the network — from member sign-ups to payouts — follows strict checks, verification steps, and ongoing monitoring.
Many MLM businesses face tense moments when someone reports an unknown login, a strange payout, or a fake account entering the system. These problems can damage trust and create fear in the team. An MLM Security Management System prevents this by monitoring every login, detecting unusual behavior, and blocking fraud before it causes damage.
Build Strong Security for All Your MLM Operations
Safeguard Information That Matter Most to Your Business
Stop breaches and data misuse with the best fraud protection MLM Security Management system.
- Give each user the appropriate level of access.
- Make sensitive data accessible to trusted upper-management staff only.
- Change user roles as your team grows.
- Record every permission update with timestamps for 100% traceability.
- Require extra checks for system and wallet access.
- Meet payment security rules with strong encryption.
- Support different options like OTPs or fingerprint scans.
- Verify every payout through a dual-authentication workflow to prevent unauthorized transfers.
- Spot suspicious logins and block them instantly.
- Get alerts on unusual transactions or profile changes.
- Let the system handle common threats automatically.
- Stay ahead of new risks with constant updates.
- Patch software automatically to fix weak spots fast.
- Run compliance scans to check security controls.
- Create reports to make audits simple.
- Adapt rules easily when regulations change.

Detect Fraud Early With Intelligent MLM Security Controls
Add advanced protection to payouts, user sign-ups, and network updates so your MLM Security Management system stays stable, compliant, and tamper-proof.
Let’s Get in TouchCreate a Safer, User-Friendly Experience for Every Member
Give Users a Clear, Secure Dashboard for Daily Work
Help distributors work with confidence. Give them encrypted MLM fraud prevention tools that cut risk, support smart choices, and protect their personal data.
Store Documents Securely with Full Access Control
Keep training files, IDs, and personal documents protected:
- Store files in encrypted sections accessible only to members.
- Lock sensitive documents after upload to prevent changes.
- Track when files are viewed or downloaded.
- Show users which documents they need to submit.
Our Features
Key Features of Global MLM Security Management
Discover how our MLM Security Management features cut risk, control sensitive actions, and keep your network transparent:
Keep Your MLM Operations Protected at Every Step
Discover how our 24/7 dedicated MLM Security Management system protects your network, your payouts, and your distributors with consistent safeguards.
Try Free DemoHow to Get Started With Global MLM Security Management?
Ready to secure your MLM operations with our MLM Security Management system? Here’s how the setup process works from start to finish:
Initial Consultation
Global MLM Software Setup and Configuration
Business Go-Live
Continuous Support and Training
Project Kick Off
End-to-End Testing
Distributor and Customer Onboarding
Initial Consultation
We begin by reviewing your current security practices, system structure, and risk areas so we can understand where protection is needed the most.
Project Kick Off
After gathering your requirements, we outline the integration plan, define timelines, and prepare the system settings specific to your business model.
Global MLM Software Setup and Configuration
Our team configures the Security Management system—setting identity checks, access rules, monitoring controls, and alert standards based on your policies.
End-to-End Testing
We validate every security layer, from user verification flows to fraud detection rules, ensuring your platform handles risks correctly before going live.
Business Go-Live
Once all checks are complete, we activate the system within your MLM platform, giving you full access to dashboards, alerts, and protective controls.
Distributor and Customer Onboarding
We help your network understand how to use the new security tools—making sure members know how to manage logins, verify identities, and protect their accounts.
Continuous Support and Training
Our team stays involved with ongoing monitoring, updates, and training so your security controls remain strong as your business grows.
What Our Clients Say?
Hear How MLM Businesses Thrive with Global MLM Software
How It Works?
How Does Global MLM Security Management Work?
Discover the concrete approach our MLM Security Management system takes to protect your MLM business:
When someone joins your network, the system assigns them a specific security role. Admins get full control. Distributors access only their data. Customers see just their orders. No one can view information they shouldn't see.
Each time a user logs in, our MLM software security system checks their location, device, and login time. If someone tries to access an account from a new country or device, the system flags it instantly. You get an alert before any damage happens.
Every transaction, message, and file gets encrypted before it moves through your system. Payment details stay locked. Commission data stays private. Even if someone intercepts the data, they can't read it.
Our MLM software security system adjustments, payout requests—everything gets logged. You can see who did what and when. Audits become simple.
The multi-level marketing security system watches for suspicious patterns automatically. Multiple refund requests from one account? Commission spike that doesn't match sales? The system catches it fast. It blocks the account and alerts you to investigate.
When users try to withdraw funds or change critical settings, the system asks for extra proof. It sends a code to their phone or email. No code, no access. This stops hackers even if they steal a password.
Our secure MLM platform checks itself for security gaps on a set schedule. It finds vulnerabilities before hackers do. Then it either fixes them automatically or alerts your team. Your protection stays strong as threats evolve.
Benefits
Advantages of Global MLM Security Management
Here’s a closer look at the strong security benefits our MLM Security Management system provides to strengthen your entire MLM ecosystem.
- Stops Financial Loss and Fraud
- Meets Compliance and Legal Standards
- Strengthens Your Brand's Reputation
- Cuts Down Manual Security Work
- Ensures Fair and Accurate Payouts
Global MLM Software is a leading MLM Software Development Company helping MLM Companies to manage and scale their MLM business.
Average Rating
Global Clients
Industries Served
Projects Completed
Countries Served
Years of Experience
Frequently Asked Questions
This FAQ has been compiled to answer some of the most frequently asked questions about our product and services. For more information, please Contact Us.
What is involved in security management in multi-level marketing (MLM)?
Security management in MLM involves protecting your network from fraud, data breaches, and unauthorized access. We provide complete network security in MLM that covers user authentication, transaction monitoring, data encryption, and compliance tracking. Our system watches every login, payment, and profile change to keep your business safe.
What are the key aspects of MLM security management in MLM Software?
Our MLM security management focuses on four key areas: access control, data protection, threat detection, and compliance monitoring. We secure your transactions with real-time fraud detection. We encrypt all sensitive data. We control who accesses what information.
What access controls are used in MLM security management?
We use role-based access control to give each user the right permissions. Admins get full system access. Distributors see only their team data. Customers access only their orders. We also provide secure MLM login with MFA authentication—users verify identity through email codes, SMS, or biometric scans before accessing sensitive areas.
How is data security implemented in MLM Software?
We implement data protection for MLM through multiple layers. First, we use SSL certificates to encrypt all data transfers. Second, we apply end-to-end encryption for critical financial information like payment details and commission data. Third, we store all files in encrypted databases. This ensures your data stays protected even if someone intercepts it.
What measures are taken to ensure MLM software security?
We provide comprehensive MLM cybersecurity solutions that include automated threat detection, activity logging, and regular security scans. Our system blocks suspicious accounts automatically. It tracks every transaction for audit purposes. It scans for vulnerabilities on a set schedule. We also offer cloud security for MLM platforms with automatic backups and disaster recovery.
How are backups handled in MLM security management?
We schedule automatic backups daily or hourly based on your needs. All backup files are encrypted and stored in secure cloud locations. If your system fails, we restore your data quickly using our disaster recovery process. We test recovery systems regularly to ensure they work when you need them most.
What is the proactive approach to security in MLM Software?
Our proactive approach means we stop threats before they cause damage. The system runs continuous security scans to find weak points. It watches for unusual patterns like multiple failed logins or sudden commission spikes. When it detects risk, it blocks the threat and alerts your team immediately. This keeps you one step ahead of attackers.
What compliance measures are followed in MLM security management?
We help you meet compliance in MLM security standards, including PCI DSS compliance for payment processing. Global MLM helps companies comply with FTC and DSA guidelines by providing transparent audit logs, secure data handling, and fraud prevention tools.
How is vulnerability management addressed in MLM security?
We address vulnerabilities through regular security assessments and automatic patching. Our MLM security management system scans your platform for security gaps every week. When it finds a weak spot, it either fixes it automatically or alerts your technical team. We also monitor security news to stay updated on new threats and update our protection accordingly.
What physical security measures are taken in MLM Software?
While our software runs in the cloud, we use data centers with strict physical security controls. These facilities have 24/7 monitoring, restricted access, and backup power systems. We also provide features required for security, like IP restrictions and device tracking, so you can control where users can access your system from.
What are the best practices for security management in MLM software?
Role-based access control should be in place to limit who can view or modify critical data. Daily automated backups protect you from data loss, while continuous log monitoring helps you spot unusual behavior early. Keeping your software updated with the latest security patches reduces vulnerabilities. Finally, regular team training ensures everyone can identify and avoid phishing attempts.
Let's Get Started





























